Mastering Docker Scout through Docker Desktop GUI and CLI
Docker Scout has made the intricate realm of container security much more navigable by presenting a cohesive look at both direct and transitive dependencies across all image layers. For a more in-depth analysis of Docker Scout’s revolutionary role in container security, I encourage you to check out my previous piece titled Docker Scout is the Game-Changer in Container Security.
In this current article, we move from theory to practice as we showcase Docker Scout in live action, allowing you to witness first-hand its innovative capabilities. I’ll demonstrate Mastering Docker Scout through Docker Desktop GUI and CLI using Docker Desktop and Command Line Interface (CLI).
Docker Scout meticulously scrutinizes the contents of an image, producing a comprehensive report outlining detected packages and vulnerabilities. Not only does it identify potential issues, but it also furnishes you with actionable remedies to address these discovered shortcomings. Additionally, Docker Scout enables you to access updates for your base image, along with suggested tags and digests. This tool further enhances your management capabilities by allowing you to filter images based on vulnerability data.
Installing Docker Scout
In order to utilize Docker Scout, it’s necessary to have Docker Desktop installed on your system. This platform is available across Linux, macOS, and Windows operating systems. The installation of Docker Desktop also comes with the Docker CLI tool, equipping you with everything you need to start using Docker Scout.
Download Docker Desktop from the official Docker website if you do not have it installed yet.
You can read more about how to install Docker Desktop on macOS in my guide “Install Docker Desktop on macOS”.
Installing Docker Scout on a Server
To effortlessly deploy Docker Scout on your server, simply execute the following command:
curl -sSfL https://raw.githubusercontent.com/docker/scout-cli/main/install.sh | sh -s --Manual Installation
Download the docker-scout binary corresponding to your platform from the latest or other releases.
- Uncompress Docker Scout as:
-
docker-scouton Linux and macOS -
docker-scout.exeon Windows
-
- Copy Docker Scout in your local CLI plugin directory:
-
$HOME/.docker/cli-pluginson Linux and macOS -
%USERPROFILE%\.docker\cli-pluginson Windows
-
- Make Docker Scout executable on Linux and macOS:
chmod +x $HOME/.docker/cli-plugins/docker-scout
- Authorize the binary to be executable on macOS:
xattr -d com.apple.quarantine $HOME/.docker/cli-plugins/docker-scout
Mastering Docker Scout via Docker Desktop GUI
Ensure that you’re operating the most recent version of Docker Desktop and navigate to the “Images” section in the menu.
In this guide, we will conduct a thorough examination of the security vulnerabilities associated with the Mattermost image.
For a more comprehensive look at how to install Mattermost using Docker Compose, I encourage you to check out my detailed guide titled, “Installing Mattermost with Docker Compose”.
Under the “Local” tab, you’ll find all the images available on your system. If you notice an absence of images, you have the option to acquire one using the docker pull command.
Click on the image that you wish to check for vulnerabilities.
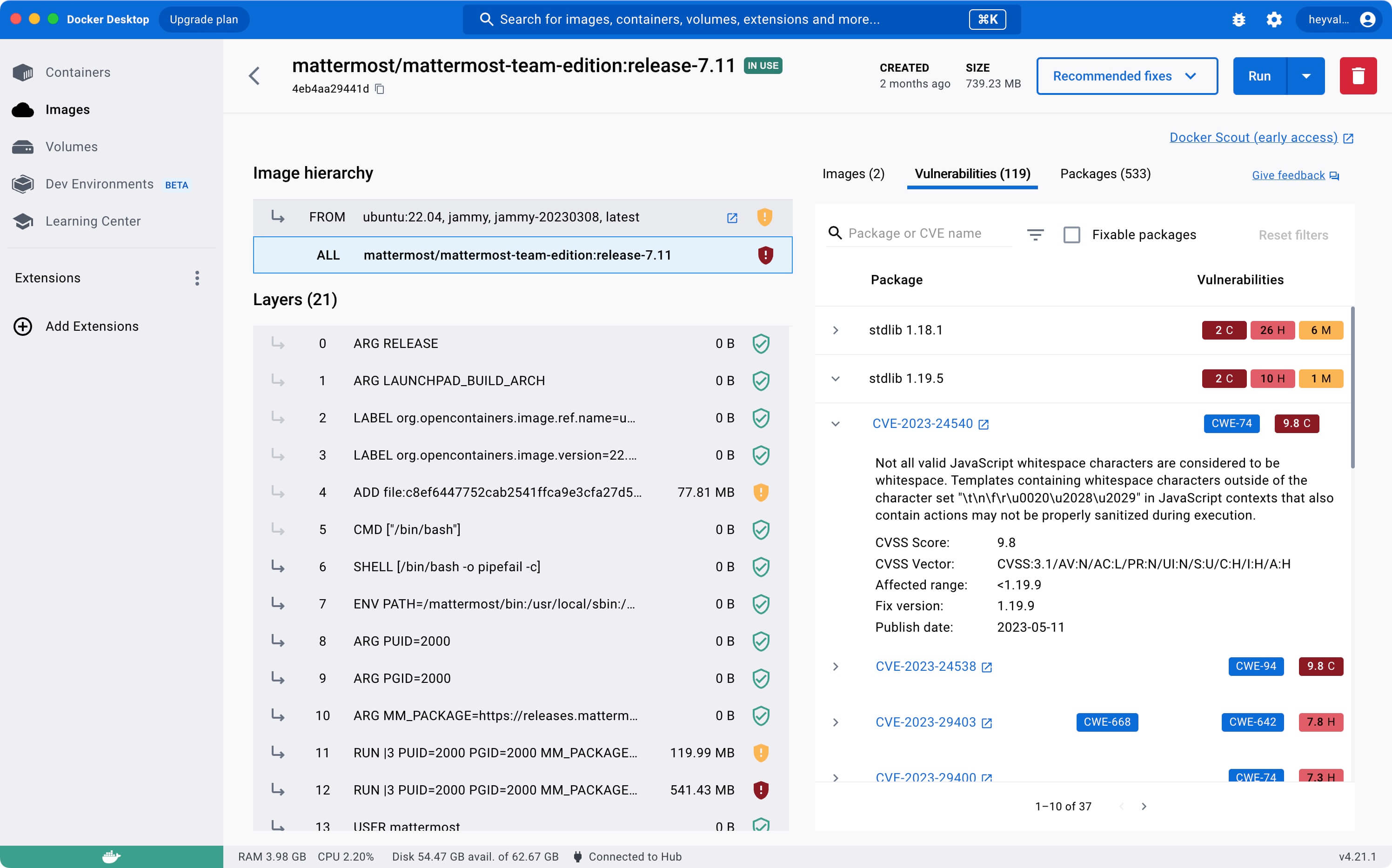
On the “Vulnerabilities” tab, you will see a report about all security issues in the image.
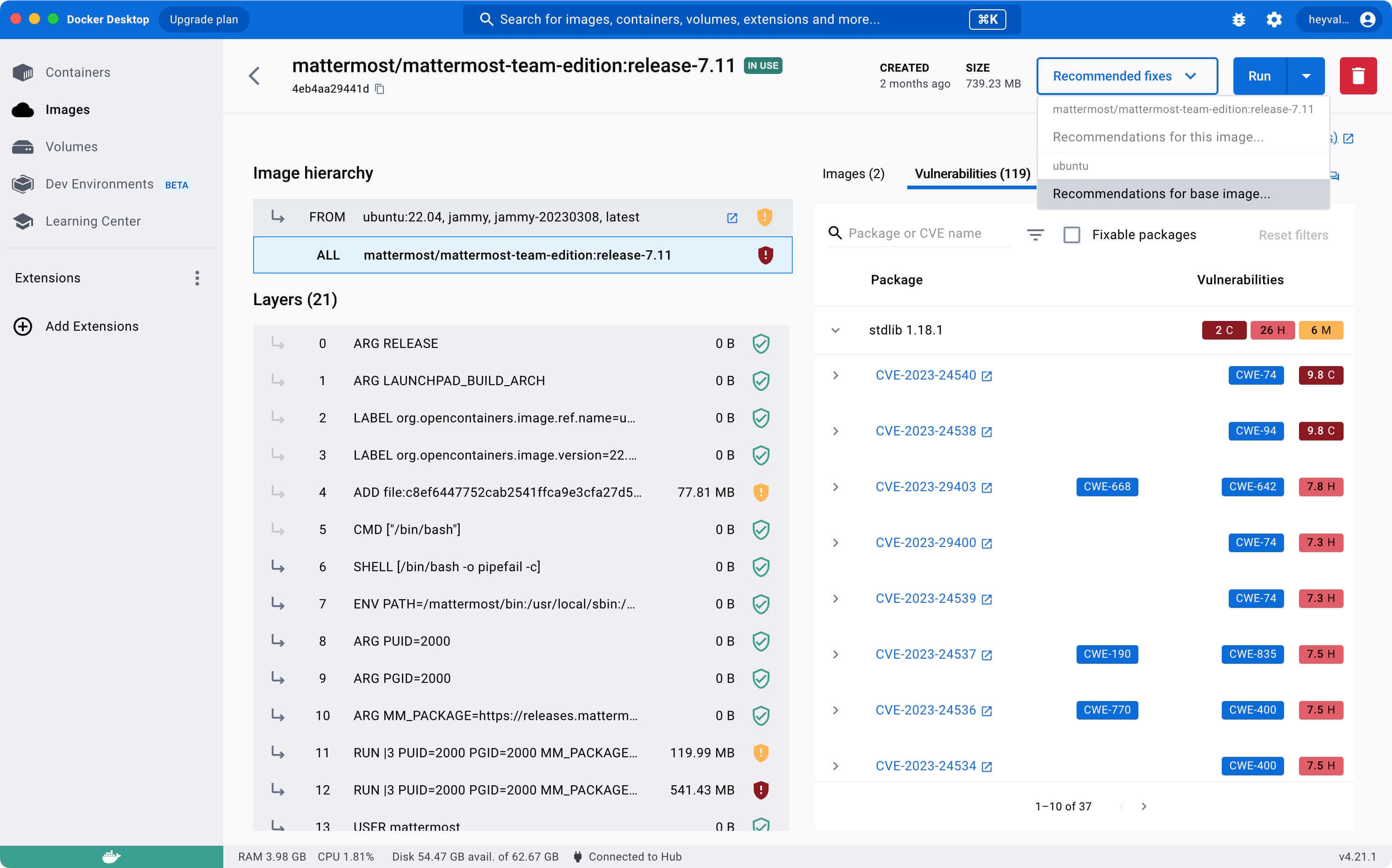
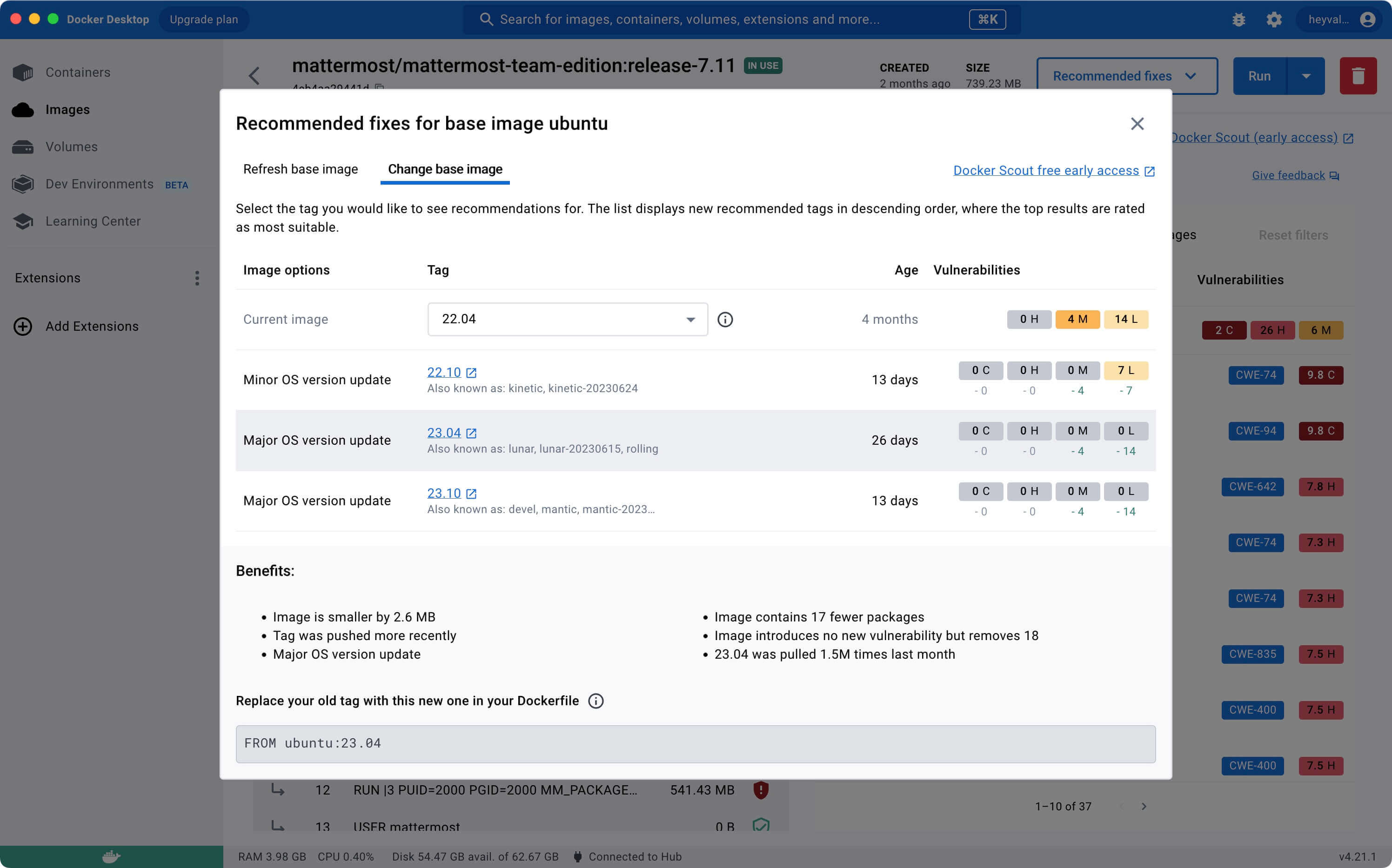
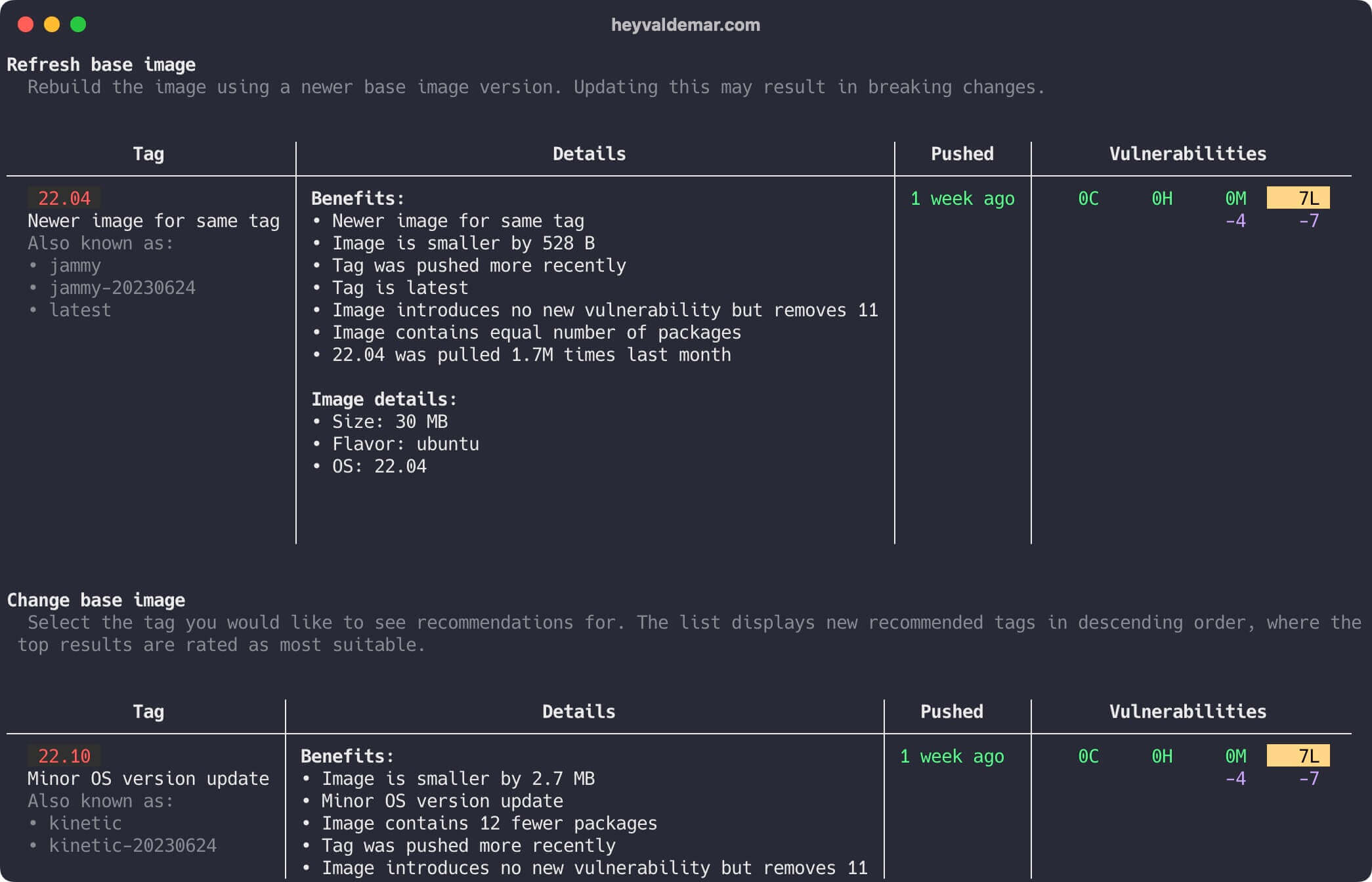
Next, you can click “Recommended fixes” and select “Recommendations for base image” to check for recommendations.
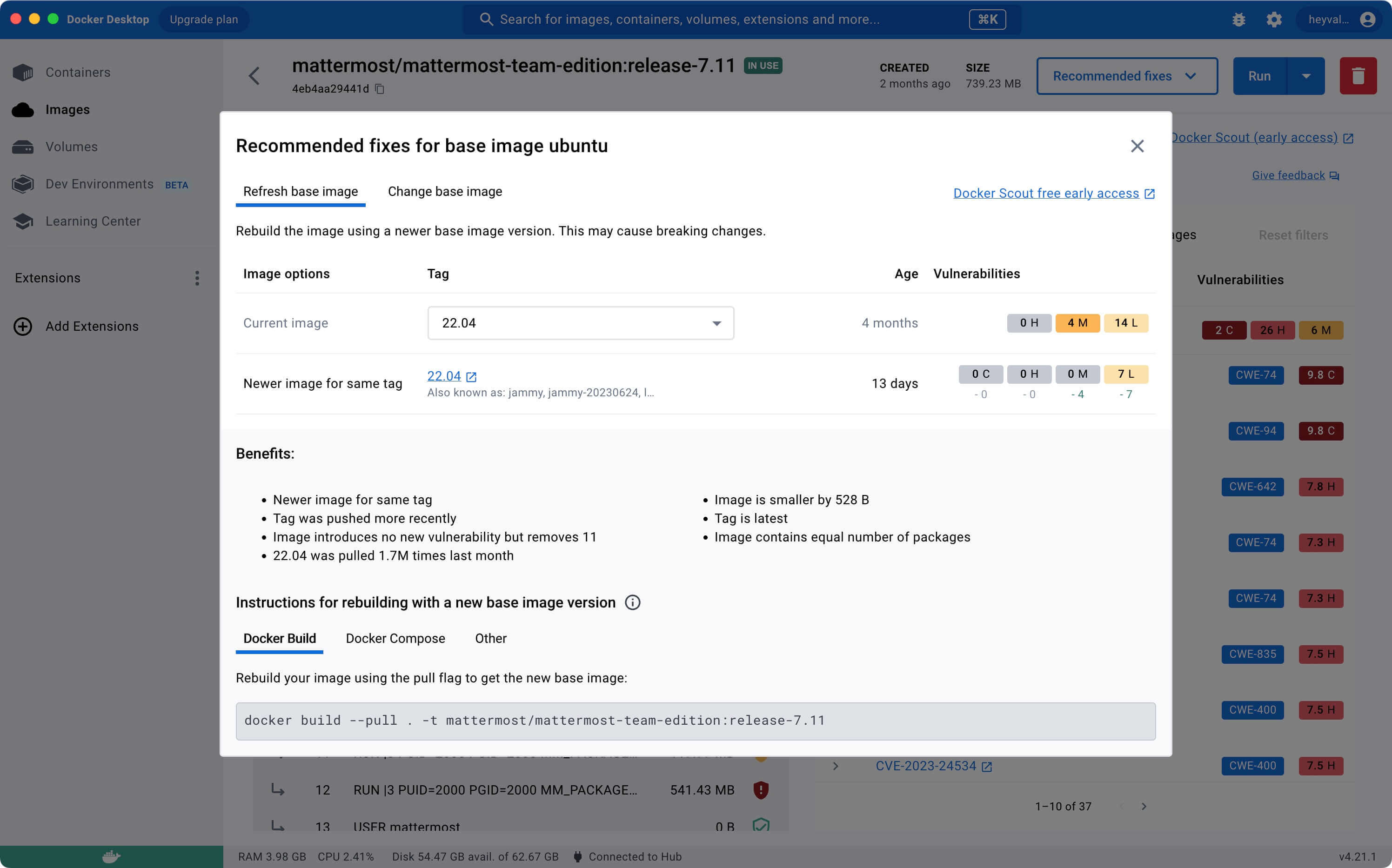
In this case, you might consider refresh your base image.
See recommendations on the “Refresh base image” tab.
Or completely change the base image.
See recommendations on the “Change base image” tab.
Mastering Docker Scout via CLI
In this part, we’ll explore some of the key commands that are integral to Docker Scout CLI’s functionality:
docker scout quickview: This command provides a succinct summary of an image, enabling you to get a quick understanding of its main features.
docker scout cves: This command reveals the Common Vulnerabilities and Exposures (CVEs) detected for any software artifacts found within an image, keeping you informed about potential security risks.
docker scout recommendations: With this command, you’ll receive a list of all possible base image updates and remediation suggestions, guiding you on how to improve your container security and efficiency.
docker scout compare: This command allows you to compare two distinct images, highlighting their differences. This feature is particularly useful when you’re tracking changes or considering updates.
By understanding and utilizing these Docker Scout CLI commands, you can significantly enhance your container management and security practices.
In this guide, I’ll be using the iTerm2 terminal emulator, installed on a macOS operating system.
We will conduct a thorough examination of the security vulnerabilities associated with the Mattermost image.
For a more comprehensive look at how to install Mattermost using Docker Compose, I encourage you to check out my detailed guide titled, “Installing Mattermost with Docker Compose”.
Let’s see a summary of an image, enabling you to get a quick understanding of its main features using the command:
docker scout quickview mattermost/mattermost-team-edition:release-7.11
Next, let’s reveal the Common Vulnerabilities and Exposures (CVEs) detected for any software artifacts found within an image using the command:
docker scout cves mattermost/mattermost-team-edition:release-7.11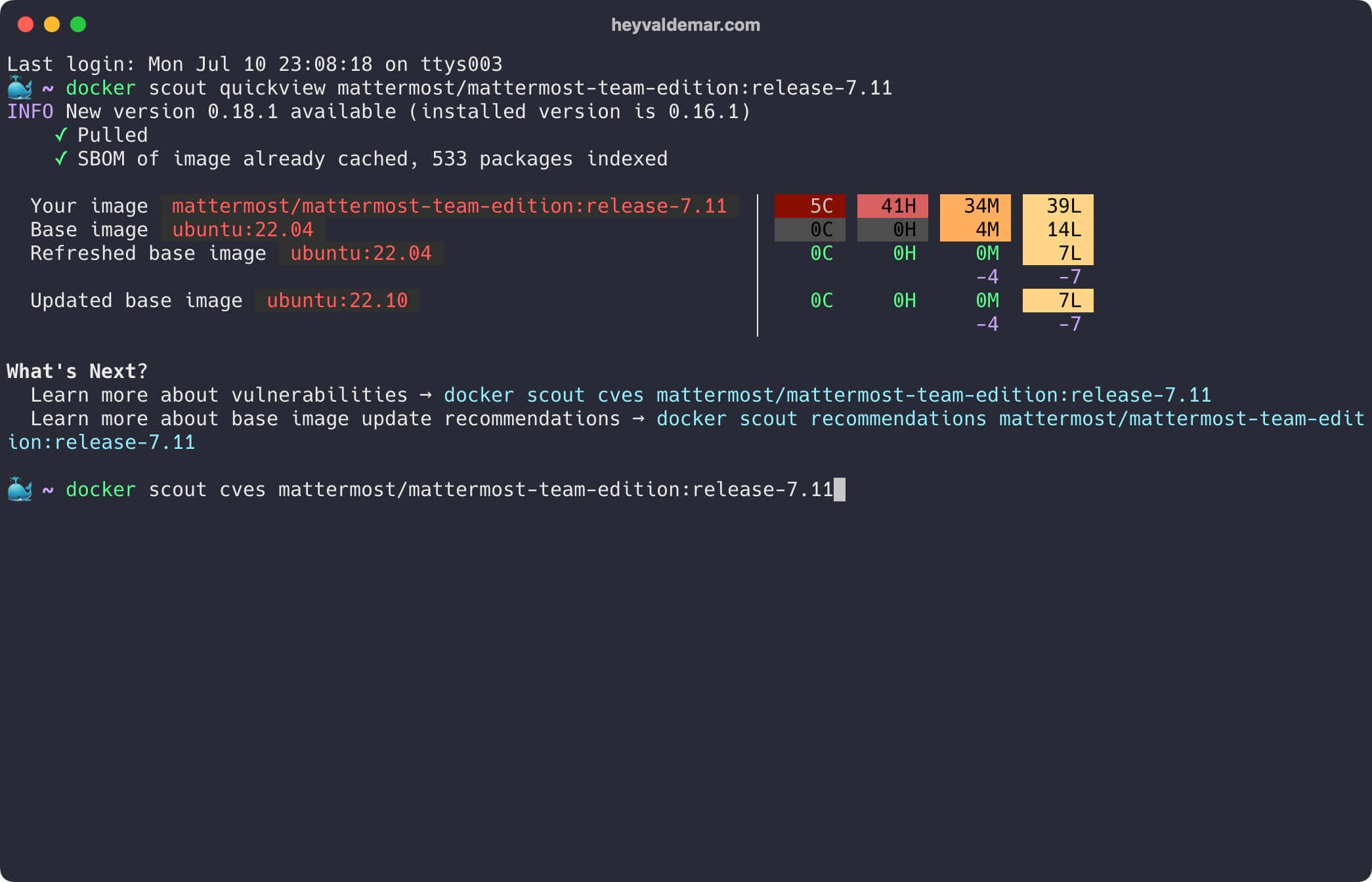
Let’s get a list of all possible base image updates and remediation suggestions using the command:
docker scout recommendations mattermost/mattermost-team-edition:release-7.11
Let’s scroll up to see more details.
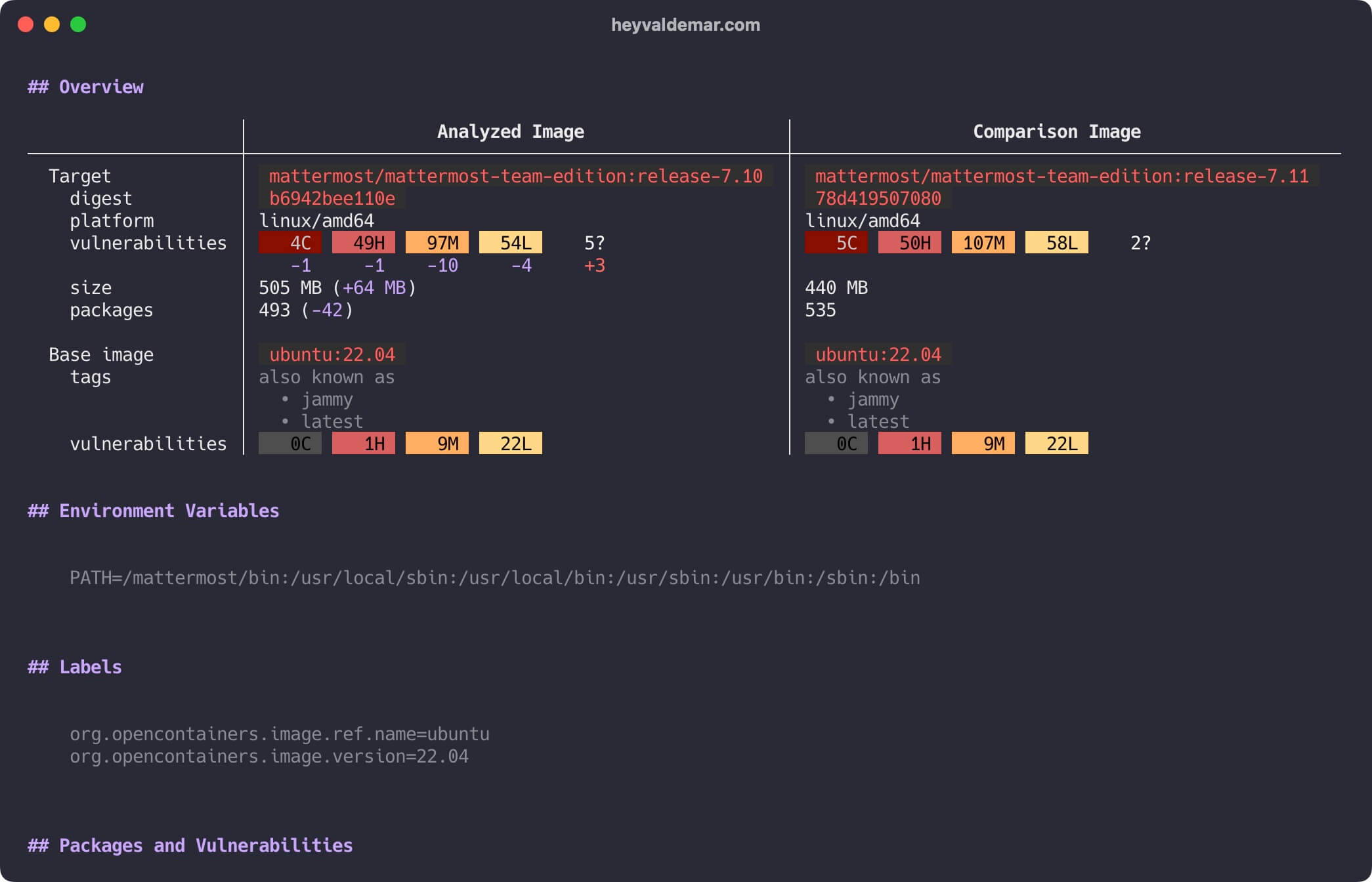
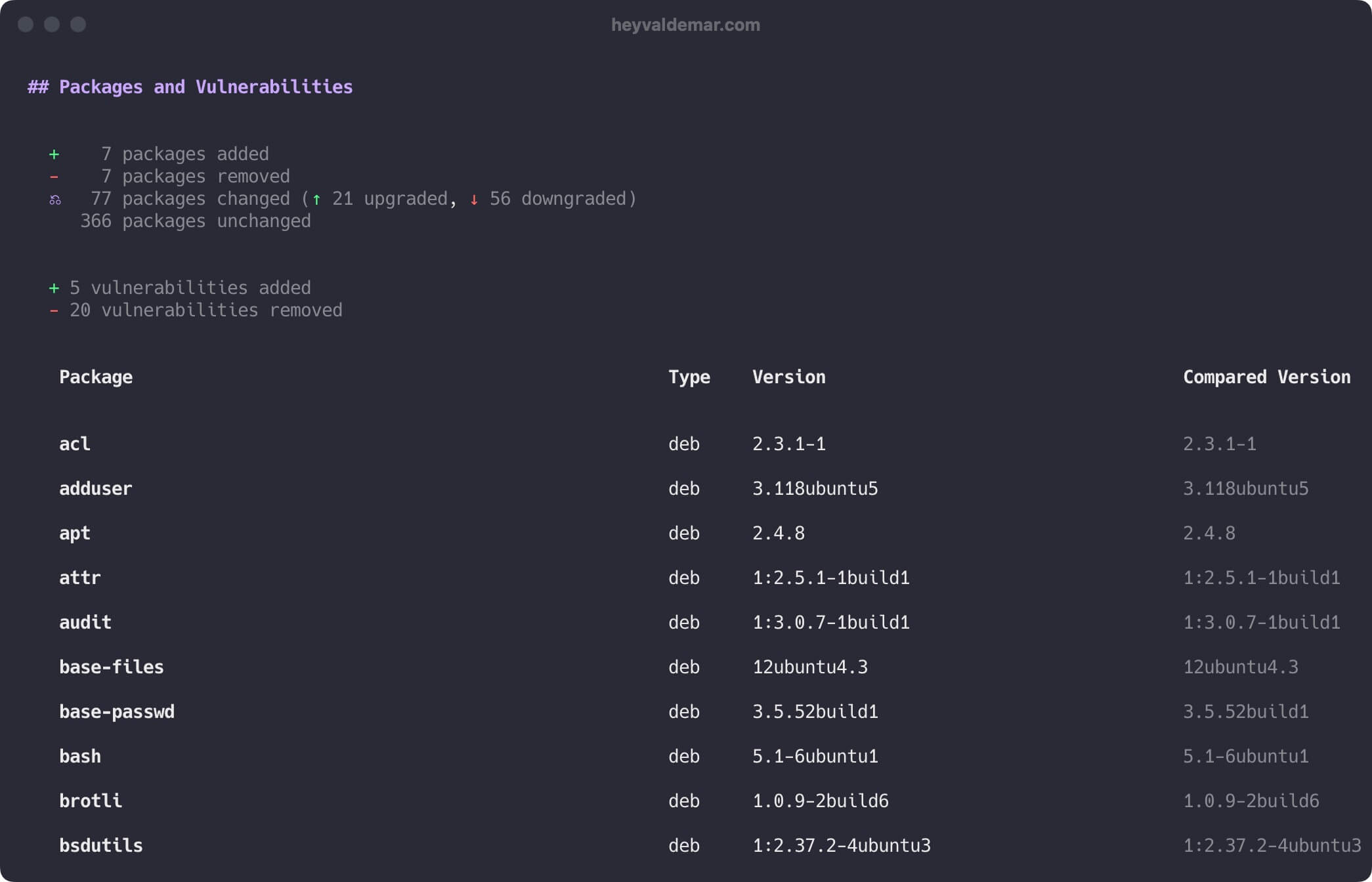
Now, let’s compare try to compare images highlighting their differences. In this case, we will compare two different releases of Mattermost.
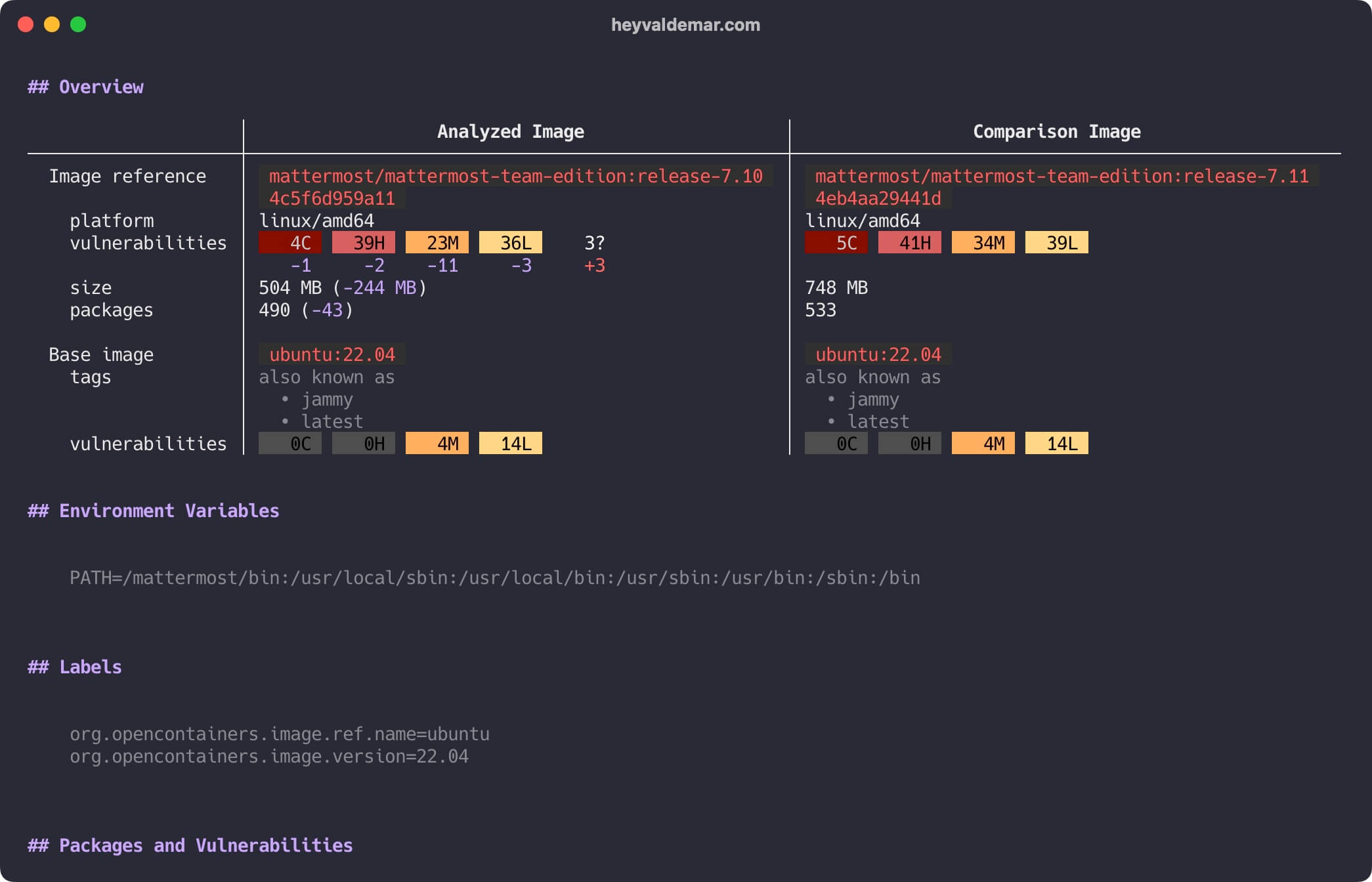
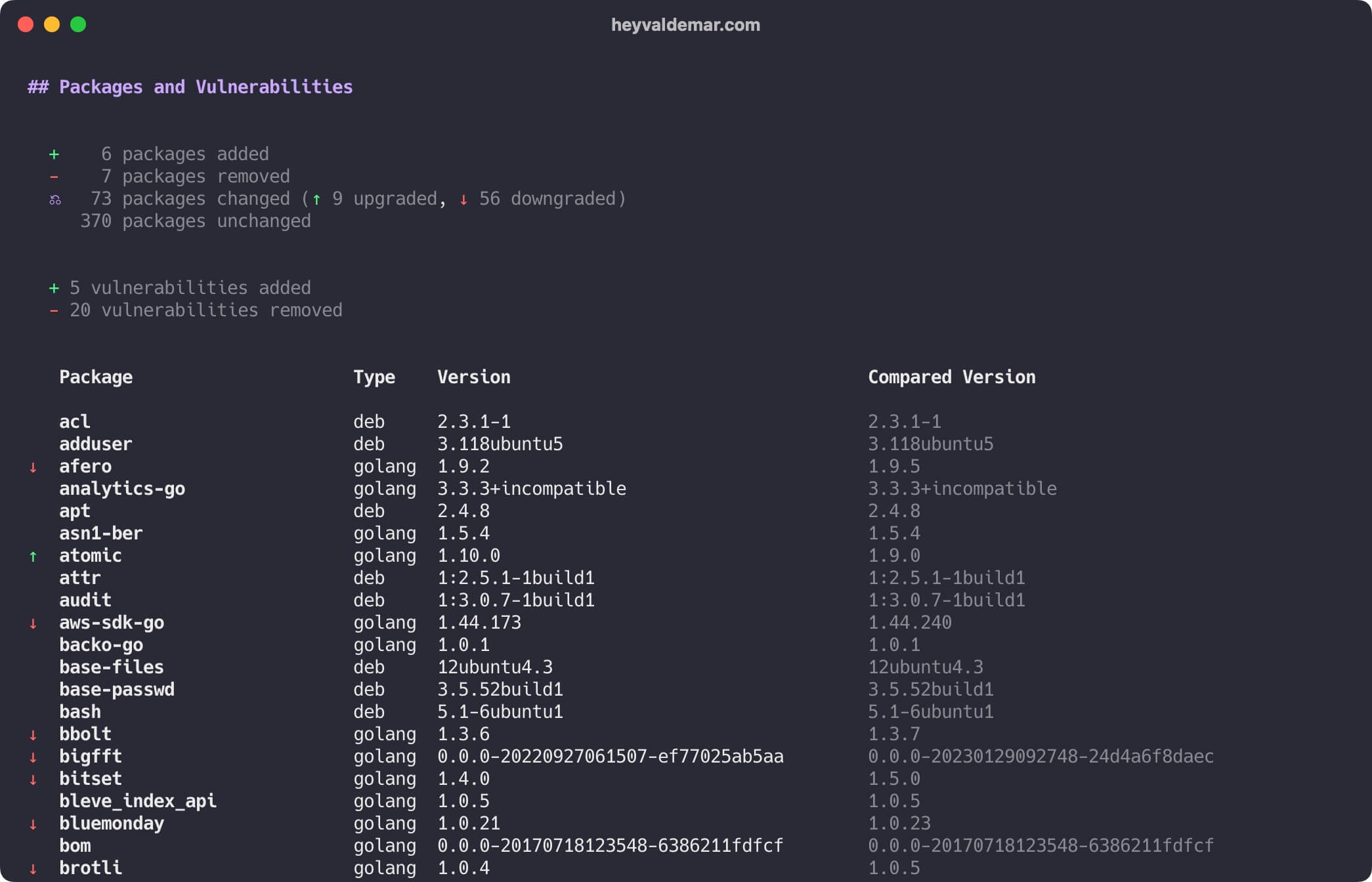
docker scout compare --to mattermost/mattermost-team-edition:release-7.11 mattermost/mattermost-team-edition:release-7.10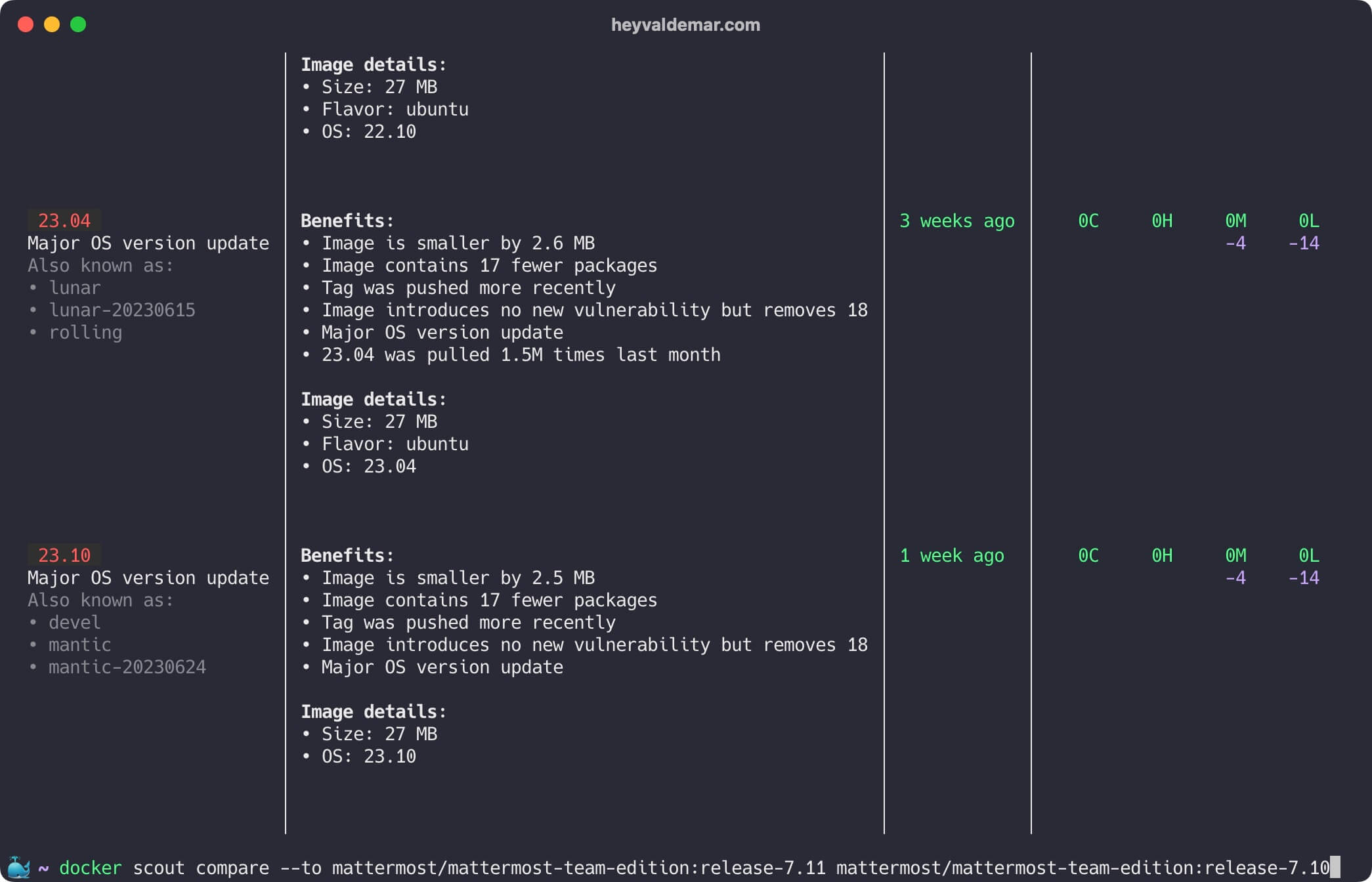
Let’s scroll up to see more details.
Mastering Docker Scout via CLI in the Container
In this part, we’ll explore a way how to use Docker Scout in the Container.
In this guide, I’ll be using the iTerm2 terminal emulator, installed on a macOS operating system.
We will conduct a thorough examination of the security vulnerabilities associated with the Mattermost image.
For a more comprehensive look at how to install Mattermost using Docker Compose, I encourage you to check out my detailed guide titled, “Installing Mattermost with Docker Compose”.
Let’s see a summary of an image, enabling you to get a quick understanding of its main features using the command:
docker run -it \
-e DOCKER_SCOUT_HUB_USER=YOUR_DOCKER_HUB_USER_NAME \
-e DOCKER_SCOUT_HUB_PASSWORD=YOUR_DOCKER_HUB_PASSWORD_OR_ACCESS_TOKEN \
docker/scout-cli quickview mattermost/mattermost-team-edition:release-7.11
Next, let’s reveal the Common Vulnerabilities and Exposures (CVEs) detected for any software artifacts found within an image using the command:
docker run -it \
-e DOCKER_SCOUT_HUB_USER=YOUR_DOCKER_HUB_USER_NAME \
-e DOCKER_SCOUT_HUB_PASSWORD=YOUR_DOCKER_HUB_PASSWORD_OR_ACCESS_TOKEN \
docker/scout-cli cves mattermost/mattermost-team-edition:release-7.11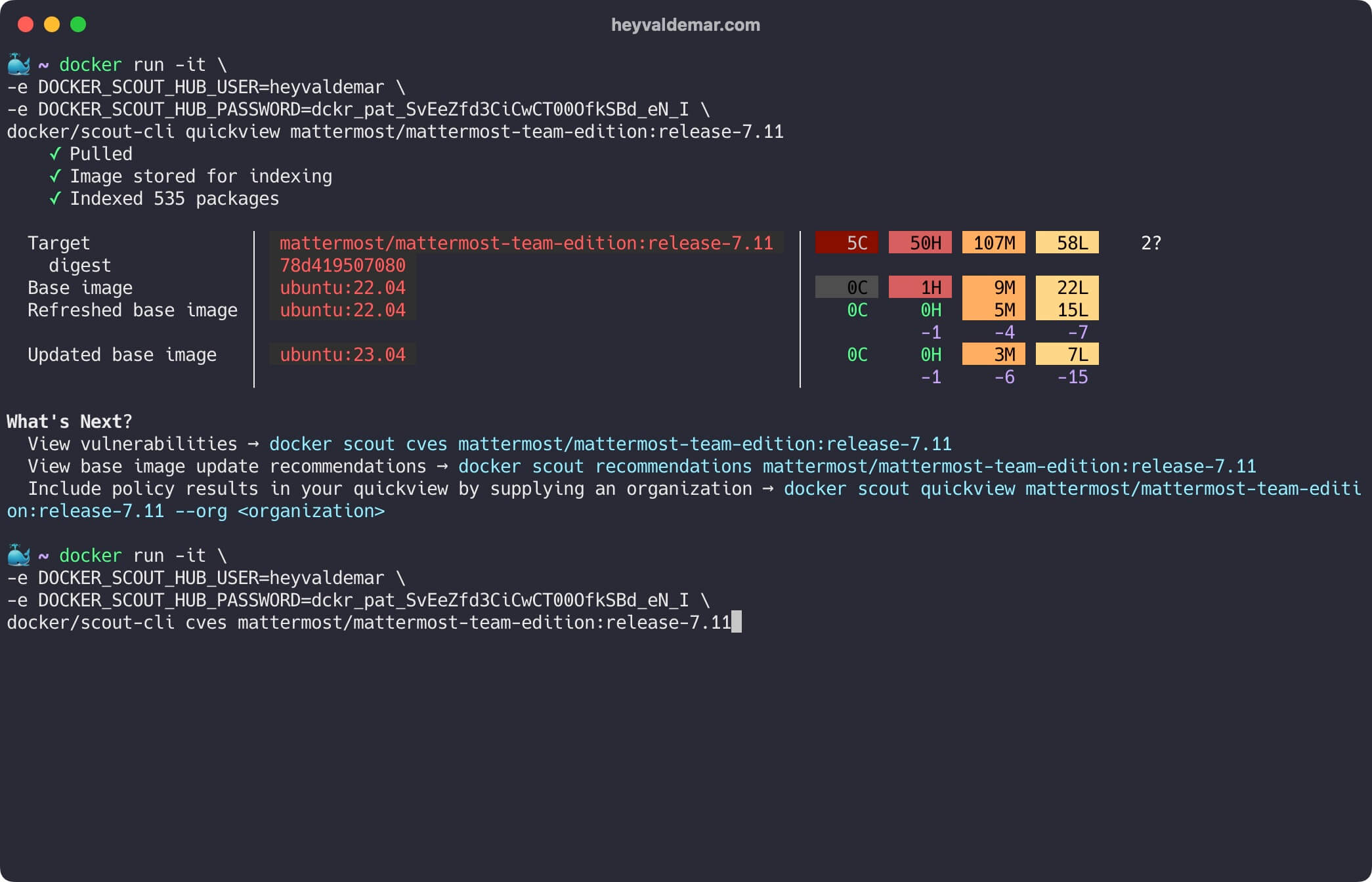
Let’s get a list of all possible base image updates and remediation suggestions using the command:
docker run -it \
-e DOCKER_SCOUT_HUB_USER=YOUR_DOCKER_HUB_USER_NAME \
-e DOCKER_SCOUT_HUB_PASSWORD=YOUR_DOCKER_HUB_PASSWORD_OR_ACCESS_TOKEN \
docker/scout-cli recommendations mattermost/mattermost-team-edition:release-7.11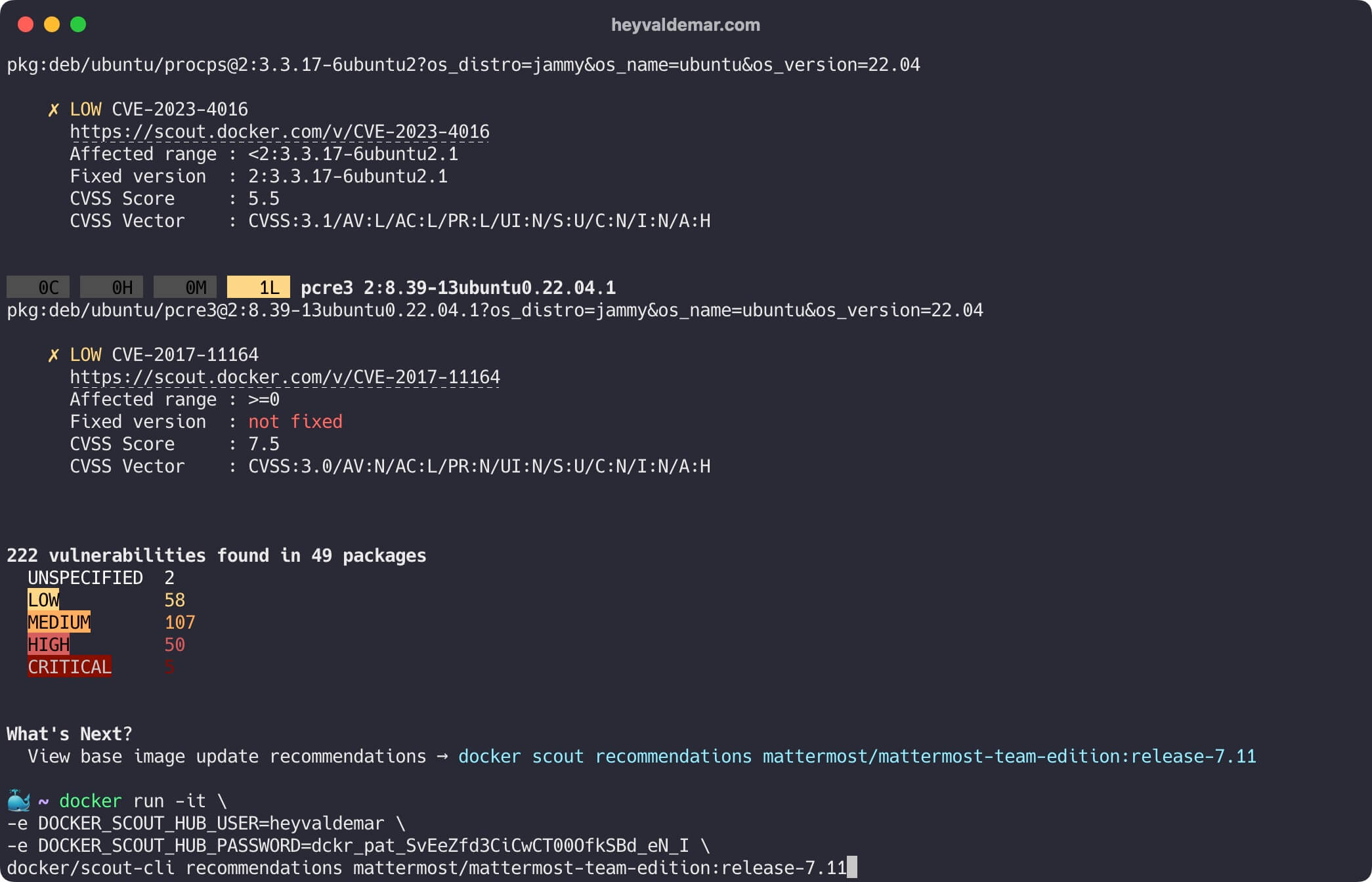
Now, let’s compare try to compare images highlighting their differences. In this case, we will compare two different releases of Mattermost.
docker run -it \
-e DOCKER_SCOUT_HUB_USER=YOUR_DOCKER_HUB_USER_NAME \
-e DOCKER_SCOUT_HUB_PASSWORD=YOUR_DOCKER_HUB_PASSWORD_OR_ACCESS_TOKEN \
docker/scout-cli compare --to mattermost/mattermost-team-edition:release-7.11 mattermost/mattermost-team-edition:release-7.10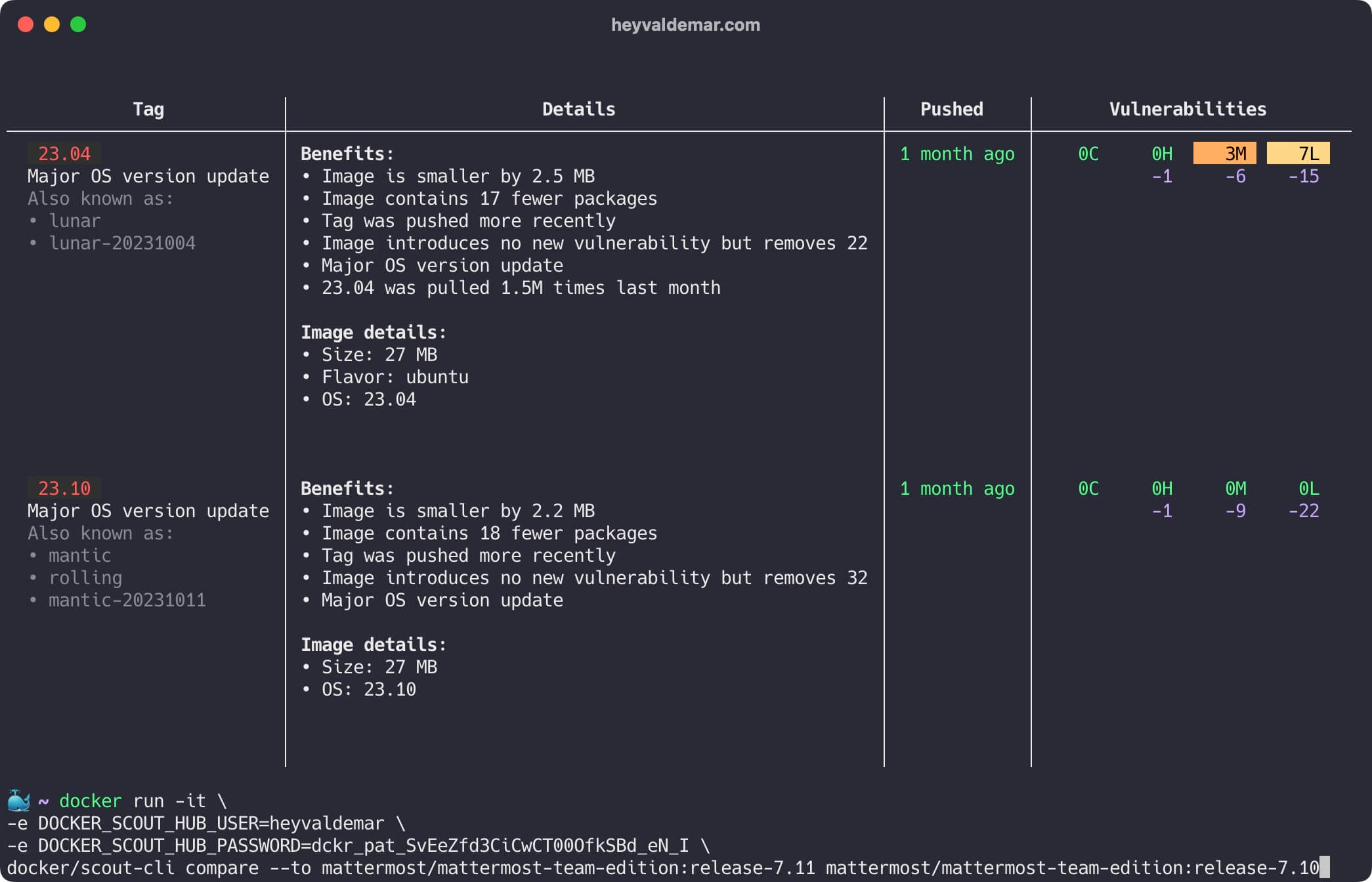
Let’s scroll up to see more details.
Conclusion
And there you have it - a comprehensive walkthrough on harnessing Docker Scout via both the Docker Desktop GUI and the CLI. If maintaining the utmost security of your containers is high on your priority list - and it certainly should be - the immediate integration of this potent tool into your workflow is highly advisable. With Docker Scout, you’re not just enhancing security; you’re investing in the resilience and robustness of your container architecture.
Follow Me
🎬 YouTube
🐦 X / Twitter
🎨 Instagram
🐘 Mastodon
🧵 Threads
🎸 Facebook
🧊 Bluesky
🎥 TikTok
💻 LinkedIn
📣 daily.dev Squad
🧩 LeetCode
🐈 GitHub
Community of IT Experts
👾 Discord
Is this content AI-generated?
Nope! Each article is crafted by me, fueled by a deep passion for Docker and decades of IT expertise. While I employ AI to refine the grammar—ensuring the technical details are conveyed clearly—the insights, strategies, and guidance are purely my own. This approach may occasionally activate AI detectors, but you can be certain that the underlying knowledge and experiences are authentically mine.
